This challenge is an awesome Single-user dungeon playing in the offices of Mandiant, part of the company organising Flare-on. When started, it shows some awesome ASCII art:
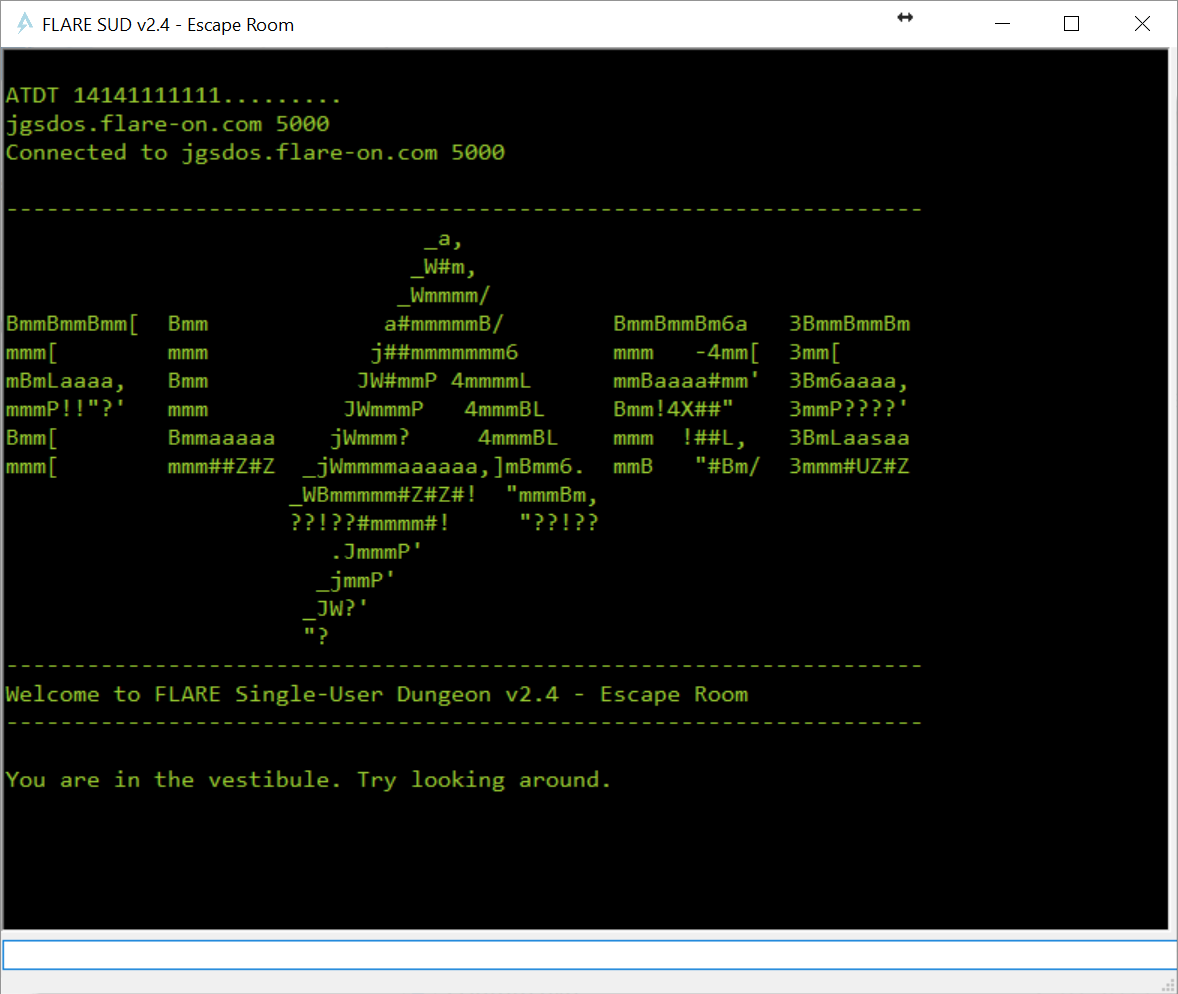
You can walk around, look around, move objects around and talk to people (although there is only one person to be found in the game, named Kevin).
Hidden in one of the drawers of the reception desk is a key. The key says:
You BANKbEPxukZfP2EikF8jN04iqGJY0RjM3p++Rci2RiUFvS9RbjWYzbbJ3BSerzwGc9EZkKTvv1JbHOD6ldmehDxyJGa60UJXsKQwr9bU3WsyNkNsVd/XtN9/6kesgmswA5Hvroc2NGYa91gCVvlaYg4U8RiyigMCKj598yfTMc1/koEDpZUhl9Dy4ZhxUUFHbiYRXFARiYNSiqJAEYNB0r93nsAQPNogNrqg23OYd3RPp4THd8G6vkJUXltRgXv7px2CWdOHuxKBVq6EduMFSKpnNB7jAKojNf1oGECrtR5pHdG1LhtTtH6lFE7IVTEKOHD+TMO1VUh0Bpa37WhIAKEwpuyp5+Tspyh0GidHtYcNWfzLNBXymmrhzvta2nJ+FtI6KWXgAAMJdUCy6YrGbWFoR2ChpeWlZLf7cQ1Awh27y6hOV19R6IKOpQzCOQLNjUplm4SOltwRU0pH6BYCeoYXbyRl3kk92uXoBsBXwxdo9QoLBOAdJmKnN95VBT03a+jS3ku3YLwXR29GIlsCfdkVKr4J1d/Xal//e+Bqq1xMEucIdnNSwr4hlOtdpLrPyfnCVkBcadlRC6hGitbptCknTCUniXCCOE1NkWSVi3v5VrXkPGAvw/iRu7F2BimC+o3tIdWPpxkcfks6zVQSiFJjVzrt28+QUb28+YRaCkPhfZALYKQLU3DR5YJw64sL40tykTI68evyRF/Fnp4VTNlWQHXPJ+Y6yCHZnrb8NdIRDPfm1wxOQJbdeaEZSa3AgqI2wW0pPBnf69vVAq4qjxyrI1LPL9hzd7cBfqnohjyDy/t78TZOh0hX++W6zkMl0Ez6I2CHxop3vzg1/9iQig0WAglmdqiAhKbDFSM7kGPf5Reyphx27uzxHAllP7LrX1vF7o9v4vcCrHE7dJpuisSWhsx3rtJsBA15mdMAbuj1ErOpWLMbXCYfhpSj6GLOHOU/PqeDoktZs9BLS+V11PcxaVVwHBGfCimMe61mSFD0hhYJXgTxbwKDvIS...
Clearly that needs to be decoded. When moving between rooms with the key on your person, something happens. When moving in the correct direction, more of the key becomes readable and a message shows:
The key emanates some warmth...
When moving in the incorrect direction, it only shows Hmm.... During a play session, if one wrong step is taken, the key stops being decoded.
Looking at the internals
The challenge wants administrator rights to run, which it probably needs for the HTTP-server it spawns using HTTP.SYS on port 9999. Opening http://127.0.0.1:9999/some/thing.asp (found in a string in the executable) comes up with a page named FAIL WHALE! with associated ASCII-art:
W W W
W W W W
'. W
.-""-._ \ \.--|
/ "-..__) .-'
| _ /
\'-.__, .__.,'
`'----'._\--'
VVVVVVVVVVVVVVVVVVVVV
Further more, the executable seems to be comprised of a few layers and other embedded executable. Searching for PE-headers in the executable comes up with a DLL that decompiles to this:
namespace flareon
{
public class four
{
private static string Decrypt2(byte[] cipherText, string key)
{
byte[] bytes = Encoding.UTF8.GetBytes(key);
byte[] numArray = new byte[16];
string str = (string) null;
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
rijndaelManaged.Key = bytes;
rijndaelManaged.IV = numArray;
ICryptoTransform decryptor = rijndaelManaged.CreateDecryptor(rijndaelManaged.Key, rijndaelManaged.IV);
using (MemoryStream memoryStream = new MemoryStream(cipherText))
{
using (CryptoStream cryptoStream = new CryptoStream((Stream) memoryStream, decryptor, CryptoStreamMode.Read))
{
using (StreamReader streamReader = new StreamReader((Stream) cryptoStream))
str = streamReader.ReadToEnd();
}
}
}
return str;
}
public static int Smth(string arg)
{
using (PowerShell powerShell = PowerShell.Create())
{
try
{
string script = four.Decrypt2(Convert.FromBase64String(arg), "soooooo_sorry_zis_is_not_ze_flag");
powerShell.AddScript(script);
foreach (object obj in powerShell.Invoke())
Console.WriteLine(obj);
}
catch (Exception ex)
{
Console.WriteLine("Exception received");
}
}
return 0;
}
}
}
Taking shortcuts
I didn’t have a lot of time for this one and had already spent an hour poking at the executable and walking around the rooms; it was pretty clear now I had to find the correct path to fully decode the key. I decided I’ll just try and brute-force it and used AutoHotkey to assist in resetting my state when I made a wrong move. About an hour of bruteforce later, my AutoHotkey script looked like this and the key was fully decrypted:
You can start to make out some words but you need to follow the RIGHT_PATH!@66696e646b6576696e6d616e6469610d0a
That hexadecimal string decodes in ASCII to findkevinmandia.
Going to Kevin and talking to him tells us:
Kevin says, with a nod and a wink: '6D 75 64 64 31 6E 67 5F 62 79 5F 79 30 75 72 35 33 6C 70 68 40 66 6C 61 72 65 2D 6F 6E 2E 63 6F 6D'.
Bet you didn't know he could speak hexadecimal! :-)
Decoding that gives us the correct flag!
